Stop Phishing and Ransomware with Next-Generation MFA
Passwordless, biometric, FIDO2, wearable authentication for the strongest access control and the greatest user convenience!
Stop Phishing and Ransomware with Next-Generation MFA
The strongest MFA with the greatest user convenience in a biometric FIDO2 wearable.
Request A Demo
.png?width=250&height=346&name=TR3-Upright-Left-Angle-large%20(2).png)

Stop Phishing and Ransomware with The Gold Standard in Identity
FIDO2 biometric next-gen MFA — in a wearable or a secure Bluetooth stick — for the strongest passwordless access control, and the greatest user convenience!
Stop Phishing and Ransomware with Next-Generation MFA
The strongest MFA with the greatest user convenience in a biometric FIDO2 wearable.
Request A Demo


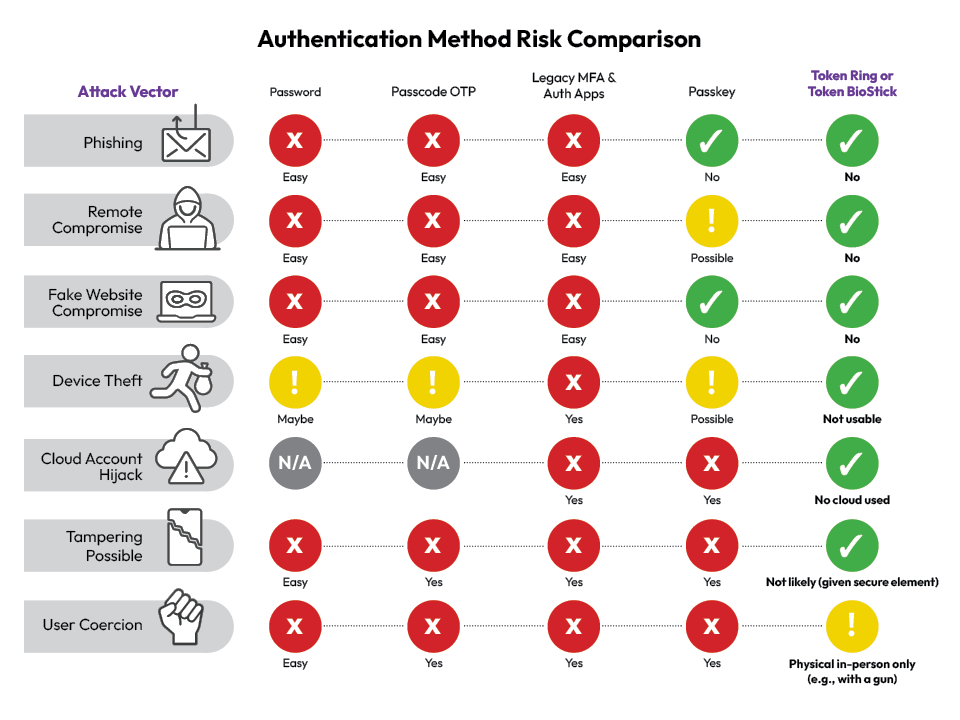
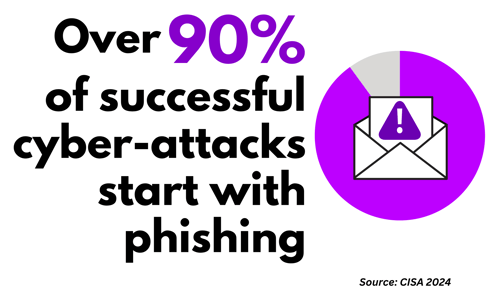
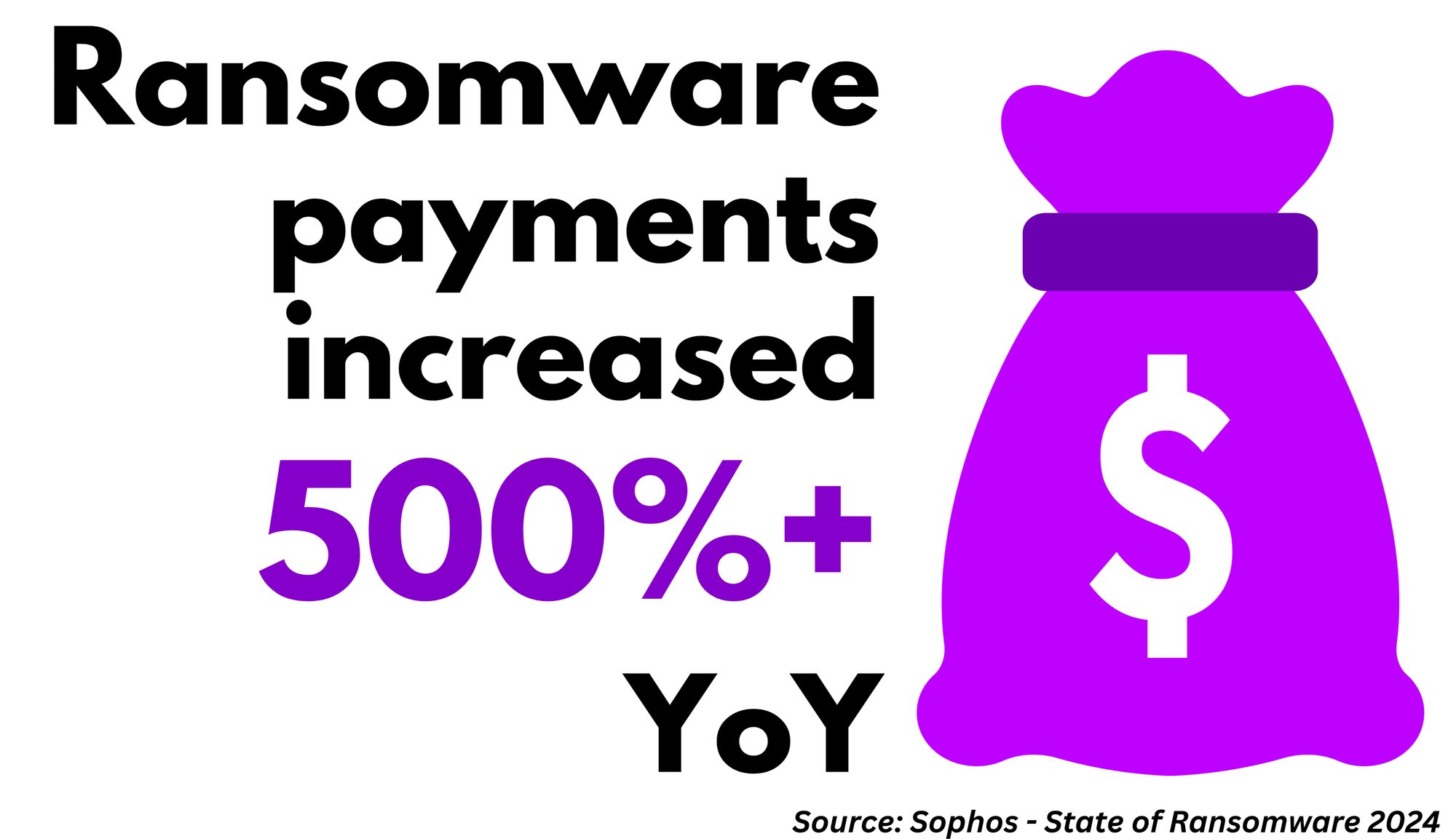
Legacy MFA is 20-Year-Old Technology
And the #1 Cause of Data Breaches and Ransomware Losses
.png?width=500&height=288&name=Your%20paragraph%20text%20(8).png)

The Only Phishing-Proof MFA Smart Solution
No OTPs to input, or credentials to remember — Token Ring and Token BioStick's integrated fingerprint sensor delivers strong identity verification in an easy to use, easy to deploy device.
- Passwordless authentication with FIDO2 Compliance
- Secure fingerprint authentication and proximity-based login
- Biometric authentication data never leaves the ring
- Integrates with all leading IAM solutions
- Token Ring eliminates vulnerabilities of BYOD in MFA













A Ton of Technology In a Tiny Footprint
Purus amet faucibus ac pulvinar ullamcorper. Sit pellentesque lacus est pharetra. Tristique enim lorem dictum curabitur in mi auctor sit vel. Bibendum sapien lectus aenean ultricies mi elementum consectetur enim nibh. Et nullam imperdiet interdum lacus amet cursus nibh egestas bibendum. Justo tincidunt sem nunc odio. Turpis tristique non pulvinar dis velit quis eu semper dignissim.
- High density laser-etched circuit boards
- 3 microprocessors
- Wafer-level chip packaging
- 2 energy efficient radios
- Highly optimized layout
- Up to 20 hours of battery life
- 83 components and 3 antennas
- EAL-5 certified Secure Element
- Advanced power management system
- 508 DPI capacitive touch fingerprint sensor
Proximity Security
NFC technology validates the proximity of Token Ring preventing man-in-the-middle attacks.
Innovative Wearable
The ring is always with the user, so it is always safe and immediately available.
Passwordless Authentication
The gesture feature allows the user to authenticate only when they intend to.
Secure Credentials
User credentials are stored on EAL5+ certified secure element for high security.
Biometric Authentication
Only the user's fingerprint will activate Token Ring meaning no one else can use it.
Insights from Industry Leaders: Our Exclusive Webcasts

WEBCAST: Prioritize Your 2026 Cybersecurity To-Do List to Maximize Your Security Posture




WEBCAST: Increasing Importance of Identity Security in the Era of The Mega-Breach and Gen AI




WEBCAST: Generative AI - A Game Changer for Infrastructure Security and Hacker Strategy


Award Winning Cyber Security




Industry Use Cases
Healthcare
Highly regulated and protected, private patient information must be awarded the highest levels of security from internal and external actors alike.
Ransomware attacks targeting healthcare organizations doubled between 2016 and 2021 and continue to rise. Current security strategies are not enough, and healthcare organizations must seek more sophisticated authentication solutions to compete.
Financial Services
With big reputational concerns, banking and finance are frequent targets for ransomware attacks, making up 22% of all attacks.
Whether infiltrating an account to move funds or collect private information, cyber criminals have their ample targets and avenues for attack. Multi-factor authentication, meanwhile, has proven insufficient for the task or protecting financial institutions.
Technology
Tech faces several key challenges in combatting ransomware attacks. Particularly, tech companies often operate in an ecosystem of vendor relationships and integrations with limited visibility into the security posture of third parties.
Ensuring the protection of customer data and the integrity of your applications requires a stronger MFA solution equipped to thwart today’s attacks.
Energy & Utilities
Attacks have increased in their destructiveness and have far-reaching consequences preventing the delivery of critical services.
In some instances, threat actors have targeted energy grids themselves creating the potential for mass disruption. Protect your customers and the energy resources they depend on by advancing beyond legacy MFA solutions.
Higher Education
The average remediation cost in higher education after a ransomware attack was higher than the global average for all sectors.
Already a heavy price, the threat to educational institutions is even more serious. Beyond sensitive student data, colleges and universities are also sites of important research that can be attractive targets for cybercriminals.
Insurance
A combination of sensitive customer data, broadening attack surfaces, and the scale of the industry itself, make insurance companies lucrative targets for cybercriminals.
The consequences of an attack go beyond remediation costs as the reputational damage and disruptions to business operations compound.
The Reviews Are In
“It is solid, phishing-resistant, authentication. It shows what the future of wearable authentication will be like, except it’s available today”
Roger Grimes
Data-Driven Defense Evangelist at KnowBe4
“This is a ground-breaking product with an exceptional team behind it.”
Tom Rivers
Solutions Architect - Large National Retailer
“I am excited about a tool that does not dangle off my belt or a clip that keeps falling off.”
Jim Panos
Executive Security Officer - Pantheon Computers
“With MFA becoming more prevalent for day to day tasks, I believe the Token Ring fills a need.”
Brett Dering
Managing Partner - Kinetic Solutions
See Token Ring In Action
Ready to see it for yourself? Drop us a line below to schedule a customized demonstration.